SharePoint Online Batch Importer
Introduction
The SharePoint Online Batch importer allows migrating documents and folders to SharePoint Online and OneDrive. Since OneDrive is based on SharePoint Online, you can use the SharePoint Online Batch importer to import documents and folders to OneDrive as well. If we refer to SharePoint Online in the following, this does apply to OneDrive as well in most cases. We will write appropriate notes in case the behavior of the importers differs for OneDrive.
The SharePoint Online Batch importer offers the following features:
Leverages Microsoft SharePoint Online Import Migration API (bulk import API)
Import documents to Microsoft SharePoint Online Document Library items
Import folders to Microsoft SharePoint Online Document Library items
Import link documents (.url files) to Microsoft SharePoint Online Document Library items
Set values for any columns in SharePoint Online, including user defined columns
Set values for SharePoint Online specific internal field values, i.e. author, editor, time created, time last modified
Set the folder path and create folders if they don’t exist
Set role assignments (permissions) on documents and folders
Import versions
Automatic or manual/custom version numbering
Set moderation/approval status on documents
Set Microsoft Information Protection (MIP) Sensitivity Labels on content files prior to uploading them to SPO
Set compliance (retention) labels on folders and documents
The SharePoint Online Batch importer is implemented mainly as a Job Server component but comes with a separate component for communicating with SharePoint Online (we refer to this component as CSOM Service because it uses the Microsoft CSOM API).
Features
The SharePoint Online Batch importer comes with the following features
The importer uses the Azure storage containers provided by SharePoint Online.
The importer only supports
import of documents with metadata (incl. role assignments) and versions,
import of folders with metadata (incl. role assignments) and
import of link documents.
The following column / field types are currently supported by the importer:
User
Text
Integer
Number
Choice and MultiChoice
Lookup
Note
DateTime
Boolean
TaxonomyFieldType
When importing documents or folders, the importer will automatically create any subfolders (of default type) needed below the configured base folder if parameter "autoCreateFolder" is set to "true".
The importer only supports setting managed metadata terms (taxonomies) by their ID in the format "{9ca5bcac-b5b5-445c-8dab-3d1c2181bcf2}".
Import into OneDrive was tested with Azure AD app-only principal authentication.
The importer supports importing files with long paths (i.e. longer than 260 characters), but you must enable this feature in the Windows operating system first (see https://docs.microsoft.com/en-us/windows/win32/fileio/maximum-file-path-limitation).
Known Issues and Limitations
Batch limitations
The importer will split the list of documents or folders to import into batches of approximately 250 items using the following rules
All objects must have the same target site & library.
A batch should contain a maximum of 250 items.
The content size of the items in a batch should not exceed 250 MB
The second rule can lead to batches with more than 250 objects. The first or last rule can lead to batches with less than 250 objects.
Delta migration limitations
If you are importing an update object to an already imported version tree with multiple verisons, if the update object fails to import, the versions of that objects are deleted from SPO. Deppending on what kind of error prevented the import of the update object, either all versions except the first one or only the last version are deleted from SPO.
Correcting the cause of the error and reimporting the update object also recreates the version tree back.
This is a limitation on how the SharePoint Migration API functions (#73681).
Other issues and limitations
Documents with 0kb content are not imported unless they are the latest version (#73672).
Created By can only be set on the first version. Later versions always inherit the value from the first version, regardless of what's set in migration-center (#73592).
Any invalid XML characters in Text and Note field values will be automatically replaced by a '_' character during import. Otherwise the import would fail with an error.
The target of a migration job must be a SharePoint Site Collection. All objects in an import job must be imported into sites / libraries in the site collection specified in the importer definition.
If you set the system rule “declareAsRecord” to “true” for an object, the importer will declare the object as a record if the target library is a Records Library - no matter how the records management is configured for that library. If you set "declareAsRecord" to "false" for an object, the import will not declare the object as record, even if automatic records declaration is enabled for that library.
Due to the asynchronous nature of the SharePoint Migration API
The progress indicator in the migration-center client works currently only on a per batch level, i.e. if you import only one batch, the progress jumps from 0% to 100% when that batch was imported. Future versions of the importer may provide a more granular progress indicator.
The migration-center database might not reflect the actual import state of the objects in the migset. For example, it might happen that objects get imported but are still marked as Validated or Error in the migration-center database. For technical details please see Technical Details on the Importer
Due to the per batch functionality of the importer, if a batch contains one or more errors, the entire batch will not be imported and all documents will be set to the error state, even those that do not contain actual errors. In order to identify the objects causing the error please consult the import run logs and the additional logs. Once the problem objects are fixed or removed from the migration set the import will be successful.
If a target site has the Document ID feature enabled: The document ID will be populated for the files imported via the migration API as well – just that it will happen asynchronously. So the DocId might be missing right after the import, but it will be populated within 24hrs (when the backend job runs).
Due to a limitation in the SPO Bulk Import API, the importer allows you to set values for choice/multi-choice fields that are not in the list of available values - even if the "fill-in" option is disabled. If you want to ensure that only allowed values are set, please use a mapping list in the transformation rules for the choice/multi-choice fields.
When setting a compliance label on a folder, all children of that folder will get the same label if no compliance label is specified for them.
When importing objects with mandatory attributes in SPO the objects will be imported and no error will be thrown even when the mandatory attributes were not set in migration-center. This is important to note as the SharePoint Online Importer, which needs to be used for delta migrations, will throw errors on import if mandatory attributes are not set.
One way to work around this limitation is to set these attributes as mandatory in the Object Type created inside migration-center. This way any empty mandatory attributes will throw errors during the Validation step.
The moderation comment cannot be set, even though it is configured in the corresponding system rule. This is a Microsoft issue in the SharePoint Migration API
Prerequisites
CSOM service
The migration-center SharePoint Online Batch Importer requires installing an additional component.
This additional component needs the .NET Framework 4.7.2 installed and it’s designed to run as a Windows service and must be installed on all machines where the a Job Server is installed.
To install this additional component, it is necessary to run an installation file, which is located within the SharePoint folder in the Jobserver instal: ...\lib\mc-spo-batch-importer\CSOM_Service\install
To install the service run the install.bat file using administrative privileges. You need to start it manually after the install. Afterwards the service is configured to start automatically at system startup.
The CSOM service must be run with the same user as the Job Server service so that it has the same access to the export location.
When running the CSOM service with a domain account you might need to grant access to the account by running the following command:
netsh http add urlacl url=http://+:57097/ user=<your user>
<your user> might be in the format domain\username or [email protected]
To uninstall the service run the uninstall.bat file using administrative privileges.
Before uninstalling the Jobserver component, the CSOM service must be uninstalled as described here.
Port access
The app-only principal authentication used by the importer calls the following HTTPS endpoints. Please ensure that the job server machine has access to those endpoints:
<tenant name>.sharepoint.com:443
accounts.accesscontrol.windows.net:443
Authentication
The migration-center SharePoint Online Batch Importer supports Azure AD app-only authentication. This is the authentication method recommended by Microsoft.
Generate Azure AD App-Only
Please follow the official Microsoft documentation for configuring the Azure AD authentication:
Using Sites.Selected permissions
In case your organization does not allow giving Sites.FullControl.All to the AppClient ID as the Microsoft documentation instructs, you also have the option of using the Sites.Selected permission instead.
However this requires additional work of specifying which sites are selected. The official Microsoft method involves using Microsoft Graph: https://learn.microsoft.com/en-us/graph/permissions-selected-overview
Alternatively you can use the Powershell library Connect-PnPOnline:
Use it in migration-center
In order to use Azure AD app-only principal authentication with the SharePoint Online Batch importer you need to fill in the following importer parameters with the information:
Configuration parameters
Values
appClientId
The ID of the migration-center Azure AD application.
appCertificatePath
The full path to the certificate .PFX file, which you have generated when setting up the Azure AD application.
appCertificatePassword
The password to read the certificate specified in appCertificateNEW TESPath.
Importer Configuration
To create a new SharePoint Online Batch Importer, go to -Importers- and press the [New] button. Then select the Adapter Type "SPOnline Batch".
Importer parameters
The common adaptor parameters are described in Common Parameters.
The configuration parameters available for the SharePoint Online Batch Importer are described below:
tenantName* The name of your SharePoint Online Tenant Example: Contoso
siteCollectionUrl* The URL of your target site collection. See SubSite vs SiteCollection for details. Examples: https://contoso.sharepoint.com/sites/MySite https://contoso-my.sharepoint.com (for OneDrive)
appClientId* The ID of either the migration-center Azure AD application or the SharePoint application. Example: ab187da0-c04d-4f82-9f43-51f41c0a3bf0 See: Authentication.
appCertificatePath* The full path to the certificate .PFX file, which you have generated when setting up the Azure AD application. Example: D:\migration-center\config\azure-ad-app-cert.pfx See: Authentication.
appCertificatePassword The password to read the certificate specified in appCertificatePath. See: Authentication.
appClientSecret The client secret, which you have generated when setting up the SharePoint application. See: Authentication.
proxyServer This is the URL, which defines the location of your proxy to connect to the Internet. Example. http://proxy.local:3128
proxyUsername The login of the user, who connects and authenticates on the proxy, which was specified in parameter proxyServer. Example: corporatedomain\username
proxyPassword Password of the proxy user specified above.
autoCreateFolder* If set the importer will automatically create the folder strcture needed for importing the object.
autoVersioning* Sets whether version numbers should be generated automatically by the importer. Enabled: The importer will generate consecutive version numbers for the versions of a document based on the versioning setting of the target library. Disabled: The user must provide appropriate version numbers for the documents using the "s__versionNumber" system attribute.
mipConfigFile Full path to the Microsoft Information Protection (MIP) configuration file, which contains additional settings for setting sensitivity labels on the content files to import. Example: C:\migration-center\mip.config See: MIP sensitivity labels
numberOfThreads* Number of batches that shall be imported in parallel. Default: 8
loggingLevel* See: Common Parameters.
Parameters marked with an asterisk (*) are mandatory.
Migset System Rules
Documents
In order to import documents, you need to create a migration set with a processing type of “<Source>ToSPOnlineBatch(document)”.
After you have selected the objects to import from the file scans, you need to configure the migration set’s transformation rules. A migration set with a target type of “SPOnlineBatch(document)” has the following system attributes, which primarily determine the content type, name and location of the documents.
mc_content_location Specify the location of a document’s content file. If not set, the default content location (i.e. where the document has been scanned from) will be used automatically. Set a different path (including filename) if the content has moved since it was scanned, or if content should be substituted with another file.
s__complianceTag Rule for setting the compliance tag for the folder. Example: INVOICE See: Compliance Labels.
s__contentType* Rule for setting the SharePoint content type of the document. This value must match a content type in the target SharePoint document library.
s__createdBy Name of the user who created the document. The value must be a unique username. Example: [email protected]
s__createdDate Sets the date and time when the document was created.
s__declareAsRecord Flag indicating if the document should be declared as a record. Record declaration will only work if SharePoint Online is the target (and not OneDrive), the target library is a Records Library and manual record declaration is enabled in the library.
s__library* Specify the title of the target library. Note: For import into a personal OneDrive use Documents as library
s__moderationStatus Sets the moderation / approval status of the document. Must be one of the following values (either the status names or their numerical value): 0 or Approved
1 or Denied 2 or Pending 3 or Draft
4 or Scheduled
s__moderationStatusComment Sets the moderation / approval status comment of the document.
s__modifiedBy Name of the user who last modified the document. The value must be a unique username. Example: [email protected]
s__modifiedDate Date and time when the document was last modified.
s__name* The name of the document including its file extension. Example: My Document.docx
s__parentFolder* The parent folder of the document. Example: /folder/subfolder
s__roleAssignments Specify role assignments for the current object. If a role definition is assigned to the current object, the migration-center SharePoint Importer breaks the role inheritance. It is possible to specify either a list of users and/or a list of SharePoint groups. If a group is specified, it is necessary, that the targeted SharePoint Group exists in your SharePoint Site. Pattern for setting single users: username;#roledefinitionname Pattern for setting groups: @groupName;#roledefinitionname Example: user;#Read @Contributors;#Contribute
s__sensitivityLabel Name of the sensitivity label to apply on the content file of the document.
Example: Confidential
Note: When applying sensitivity labels, you also need to specify the path to an additional MIP configuration file. See: MIP sensitivity labels.
s__site* Specify the target (sub-)site for the document. Note: The Site name is case sensitive.
Example: My Site or My Site/My SubSite
For OneDrive: use /personal/<your personal site> Example: /personal/donald_duck_onmicrosoft_com
s__versionNumber Sets the version number of the document. Must be in the format: x.y Example: 1.0
Mandatory if importer parameter "autoVersioning" is set to "false".
Specified value will be ignored if parameter "autoVersioning" is set to "true".
target_type* Rule for setting the association with a migration-center Object Type. Validation will be done based on this system rule.
Links
SharePoint Online supports documents with the file format ".url". We call these documents "link documents" since they do not have real content but just point to another document in SharePoint Online or to an external web site. The importer will create the necessary content of the link documents on the fly and save them in the following folder: <mc log folder>/SPOnline Batch Importer/<job run id>/link_files. Thus, the importer will ignore the content of any source object that is imported as a link document because it will import the generated link content instead.
In order to import link documents, you need to create a migration set with a processing type of “<Source>ToSPOnlineBatch(link)”.
After you have selected the objects to import from the file scans, you need to configure the migration set’s transformation rules. A migration set with a target type of “SPOnlineBatch(link)” has the following system attributes, which primarily determine the content type, name and URL of the linked documents or web site respectively.
Compared to the Documents migset, the Link migset is missing the mc_content_location, s__complianceTag, s__declareAsRecord, s__moderationStatus, s__moderationStatusComment, s__sensitivityLabel system rules and has the following new rules:
s__url* The target URL of this link document. Can be a URL to another SharePoint document or a URL to an external web site.
Example:
https://contoso.sharepoint.com/sites/MySite/Documents/Test.docx
Example of how to obtain the URL of an object that was already migrated into SharePoint Online using the SPO Batch Importer using a getDataFromSQL function:
Folders
In order to import folders, you need to create a migration set with a processing type of “<Source>ToSPOnlineBatch(folder)”.
After you have selected the objects to import from the file scans, you need to configure the migration set’s transformation rules.
A migration set with a target type of “SPOnlineBatch(folder)” has the following system attributes, which primarily determine the content type, name and location of the folders.
Compared to the Documents migset, the Folder migset is missing the mc_content_location, s__declareAsRecord, s__moderationStatus, s__moderationStatusComment, s__sensitivityLabel and s__versionNumber system rules, and has no additional ones.
Delta migration
Starting with version 24.3 of migration-center, the SharePoint Online Batch Importer has Delta migration capabilities.
You can import newly scanned versions and updates to documents that have been previously imported into SharePoint Online using the Batch Importer.
Technical details
Because the Batch Importer uses Microsoft SharePoint Migration API, there are a few things to consider about how the delta migration process works in the Batch Importer:
When importing a new version or an update to an already imported document in SharePoint, migration-center has to include the already imported objects from migration-center with their metadata and content. For example: importing 1 update object to an already imported document that has 10 versions, migration-center will send to SharePoint the 11 objects representing all of them, even though the 10 versions are already marked as imported.
This has the following implications:
Importing new versions and updates might take longer than expected if the already imported version trees are big
The importer log will display the total number of imported objects and in parenthesis the current updates and new versions
It is important that the originally imported documents are not reset or removed from the migset when doing a delta migration. The new versions and updates should be added to a copy of the original migset.
Please also note the Delta Migration Limitations.
MIP sensitivity labels
The SharePoint Online importer supports applying Microsoft Information Protection (MIP) sensitivity labels on the content files before they get uploaded to SharePoint Online. To learn more about sensitivity labels, please see https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide.
Register an Azure AD app
The MIP software development kit provided by Microsoft that we use to apply the sensitivity labels on the content files requires you to register an application in your Azure AD. You could use the same app as in Azure AD app-only principal authentication or setup a separate application as described here: https://docs.microsoft.com/en-us/information-protection/develop/setup-configure-mip#register-a-client-application-with-azure-active-directory
You need to create a client secret for your registered application and configure the following access permissions:
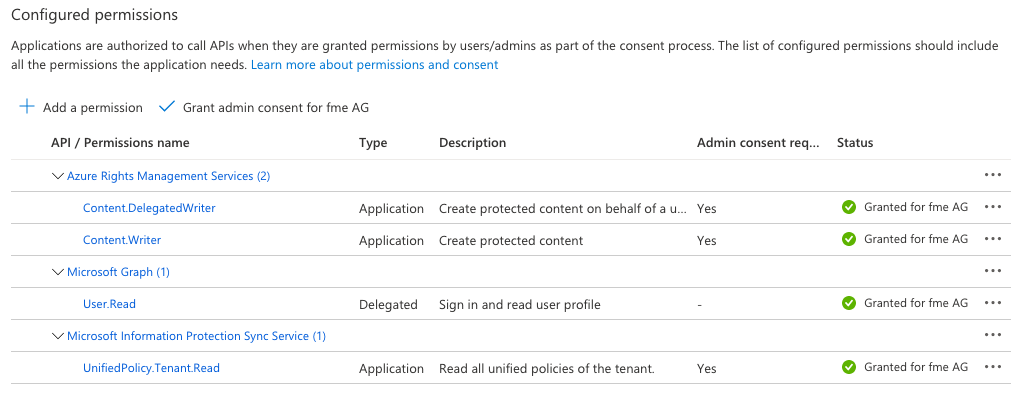
Install VC++ Runtime
The Microsoft MIP SDK also needs the VC++ runtime installed on the job server machine to work properly. You might get a LoadLibrary failed for: [C:\fme AG\migration-center Server Components 3.15\lib\mc-sharepointonline-importer\MIPService\x86\mip_dotnet.dll] error if the VC++ runtime is missing and you want to apply sensitivity labels on your documents.
For your convenience, we provide the VC++ runtime installers in the lib\mc-sharepointonline-importer\MIPService\VC_Redistributables folder of your MC job server installation. Which variant to install (i.e. x86 or x64) depends on your .NET configuration. Usually you should install the x86 VC++ runtime (even on a x64 system). If that does not work, you should install the x64 variant.
Create the configuration file for the importer
The SharePoint Online Batch importer requires you to provide several configuration parameters in a XML configuration file. You can find a template configuration file (template-mip.config) in the lib\mc-spo-batch-importer folder of your migration-center job server installation.
Create a copy of the template file, fill in the required information from your Azure AD app that you had created in the previous step, and enter the full path to your config file in the mipConfigFile parameter of your SharePoint Online Batch importer. The result should look similar to the following:
We provide a Java based command line tool for encryption, which you must use to encrypt the Azure.App.Secret value before you put it in the configuration file. To encrypt the secret, proceed as follows:
Open a command line window on the job server machine.
Switch to the
migration-center Server Components <version>\lib\mc-corefolder, e.g.migration-center Server Components 3.16\lib\mc-coreRun the following command:
java -cp mc-common-<version>.jar de.fme.mc.common.encryption.CmdToolThe tool will ask for the text to encrypt. Enter or paste the secret value and press enter.
The tool will output the encrypted text. Copy and paste it into the configuration file.
Compliance Labels
Compliance labels are managed in the MS 365 compliance center, which you can access with the following URL: https://compliance.microsoft.com/
For more details about creating and publishing compliance labels, please see https://docs.microsoft.com/en-us/microsoft-365/compliance/create-apply-retention-labels?view=o365-worldwide
You can assign any label that is published for the target SharePoint site to the folders and documents in a migration set. The migration-center provides a new system rule for setting compliance labels:
s__complianceTag
If you want to set a label on a document or folder, it is mandatory to specify the label name in the "s__complianceTag" system rule.
The importer will check before importing the object if the specified label is available in the target site and throw an error if it is not in the list of available labels.
Hierarchical
To set compliance labels that are stored in a hierarchical fasion in MS 365 compliance center, you can use the GUID of the label in the s__complianceTag system rule.
Technical Details on the Importer
This chapter will give you an overview of the importer’s operating principle.
Overview
Each SharePoint Online Batch Importer job will go through the following steps:
Split the list of objects to import into batches of approximately 250 objects.
For each batch repeat
Generate the XML files (e.g. Manifest.xml etc.) necessary for submitting the batch to the SharePoint Migration API.
Upload XML files and content files of the batch to an Azure BLOB container storage.
Submit the import batch to the SharePoint platform as a migration job.
Monitor the progress of the migration job.
When the migration job has finished, verify that all objects submitted for import were successfully imported by retrieving them by ID and save the result of the verification back to the migration-center database.
Depending on your job configuration, several batches are imported in parallel (see “numberOfThreads” parameter in the import job configuration).
Tracing imported objects
The SharePoint Online Batch Importer will store the following information for imported objects in the MC database, which will allow you to trace an imported object back to the corresponding source object.
Attribute in MC database
Value
ID_IN_TARGET_SYSTEM
String that consists of the following components:
<list item id>|<library guid>[|<version number>]
The version number component is optional. These information will allow you to uniquely identify the imported object in the target system.
Example values:
387088|d69e991b-d488-49bb-b739-858669e60b19|1.0
384956|d69e991b-d488-49bb-b739-858669e60b19
OBJECT_INFO1
Server relative URL to the object.
Example values:
/teams/bu6/TestLibrary/Test
/teams/bu6/TestLibrary/Test/Document.txt
Note: OBJECT_INFO1 is an internal column in the SOURCE_OBJECTS table and not visible in the MC client.
Please note that the URLs in the OBJECT_INFO1 attribute will only be valid for the latest version in a version tree because SharePoint uses different URLs for latest versions and old versions.
For example, if the document from the example above had two versions 1.0 and 2.0, both values in OBJECT_INFO1 would be:
/teams/bu6/TestLibrary/Test/Document.txt
But the correct URL for version 1.0 would be: /teams/bu6/TestLibrary/_vti_history/512/Test/Document.txt
XML files
The SharePoint Import Migration API requires the following XML files for each import batch:
ExportSettings.XML
LookupListMap.XML
Manifest.XML
Requirements.XML
RootObjectMap.XML
SystemData.XML
UserGroupMap.XML
ViewFormsList.XML
For more details on those files, please see https://docs.microsoft.com/en-us/sharepoint/dev/apis/migration-api-overview#import-package-structure
SubSite vs SiteCollection
The siteCollectionUrl parameter in the importer requires the URL of a SiteCollection, not a SubSite.
SiteCollections have their own permissions and access. Consider the following two SiteCollections:
https://contoso.sharepoint.com https://contoso.sharepoint.com/sites/MySite
If the appClientID was created for https://contoso.sharepoint.com/sites/MySite but in the importer siteCollectionUrl you are setting https://contoso.sharepoint.com you will receive a 401 Unauthorized error.
How to tell if a site is a SiteCollection or a SubSite
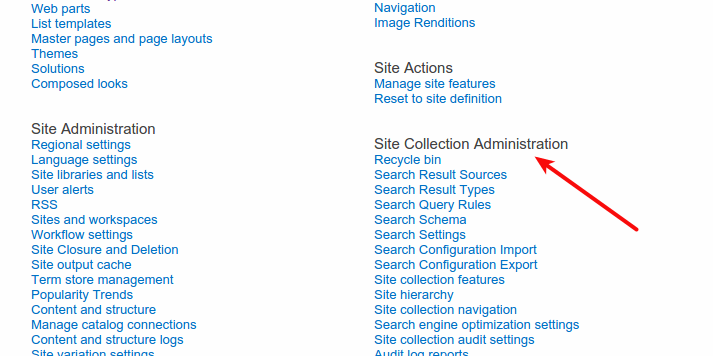
Go to the site you are trying to import into, select Site Contents and then Site Settings.
If you see the Site Collection Administration groups with all relevant links as in the image below then it means you are on a site collection.
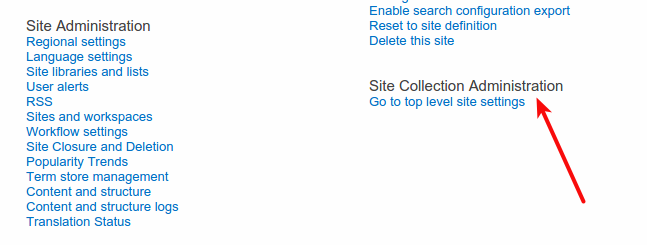
If you see the Site Collection Administration with a single link saying Go to top level site settings as in the image below then you are on subsite.
Additional Logs
Additional log files generated by the SharePoint Online Batch Importer can be found in the Server Components installation folder of the machine where the job was run, e.g. …\fme AG\migration-center Server Components <Version>\logs\SPOnline Batch Importer\<job run id>
You can find the following files in the <job run id> folder:
The import-job.log contains detailed information about the job run and can be used to investigate import issues.
The generated manifest files for each batch in the <batch number>/manifest sub-folder.
The log files generated by SharePoint Online for each batch in the <batch-number>/spo-logs sub-folder.
The content files generated for link documents in the <batch number>/link_files sub-folder.
Last updated
Was this helpful?

